Security Services
Safeguard your business against digital threats and ensuring data protection and compliance with our comprehensive cyber security services
Home » Managed Services » Security
Let’s talk about security
With information Technology being a fundamental part of business operations, and digital transformation a necessity, it’s crucial to have access to high-caliber and experienced cyber security experts to ensure that you are taking appropriate steps to ensure the continued e-safety of your organisation. Our service also ensures you’re never without a cyber security advisory when it comes to your governance obligations.
Did you know..
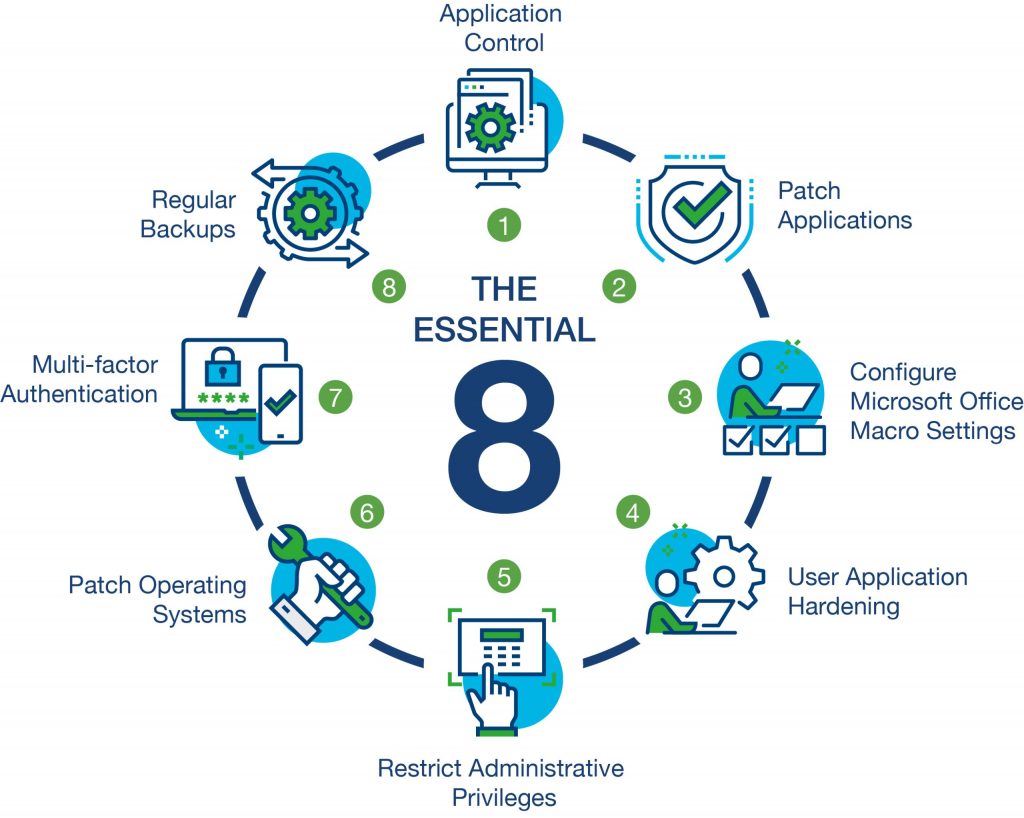
What is the Essential 8
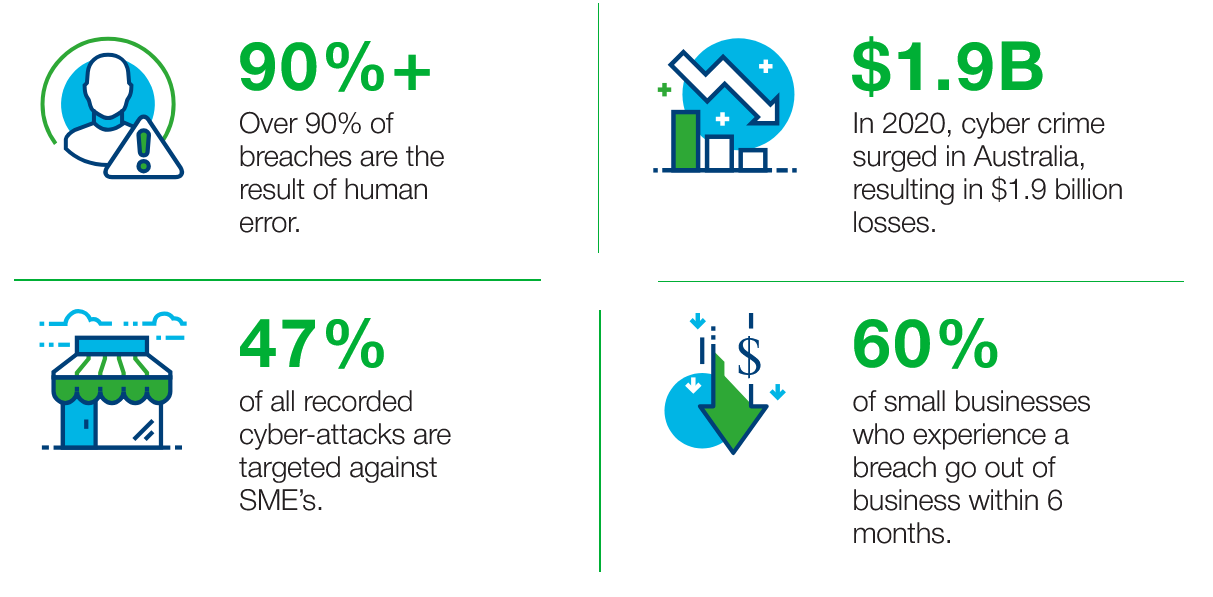
Why every business needs cyber security
Implementing cyber security measures in a company is crucial for safeguarding sensitive information, maintaining trust with customers, and preserving the organization’s reputation. With the increasing frequency and sophistication of cyber threats, protecting against data breaches, malware, and other cyber attacks is essential for business continuity. Effective cyber security measures not only mitigate financial risks associated with data breaches but also ensure compliance with regulatory requirements. By prioritizing cyber security, companies demonstrate their commitment to protecting valuable assets, fostering customer loyalty, and sustaining long-term success in an ever-evolving digital landscape.
The time to act is now
There’s no better time than now to take proactive steps and gain the reassurance that your business is safeguarded and secure.
Otherwise you may be faced with:
- Data breaches and loss of sensitive information
- Financial losses due to theft or manipulation of data
- Legal liabilities and regulatory non-compliance
- Disruption of business operations and loss of productivity
- Damage to the company’s reputation and trustworthiness
FAQs
Cybersecurity involves protecting computer systems and data from unauthorised access and attacks. It’s vital for businesses as it ensures the security of sensitive information, maintains customer trust, and prevents financial and reputational harm from cyber threats. Implementing robust cybersecurity measures is essential for safeguarding operations and complying with regulatory standards in today’s digital landscape.
To secure your small to medium business’s data, use strong security measures like firewalls and encryption, educate staff on cybersecurity, control access to sensitive information, back up data regularly, monitor for threats, and stay updated on cybersecurity practices and regulations. These actions help protect your business from potential cyber threats and ensure data integrity and confidentiality.
Recent cybersecurity trends include increased ransomware attacks, zero-day vulnerabilities, and cloud security risks. Artificial intelligence and machine learning are shaping both attacks and defences, while IoT vulnerabilities and persistent phishing threats remain significant concerns. Adapting to evolving regulatory requirements is crucial for maintaining robust cybersecurity measures against these dynamic challenges.
To safeguard your business from ransomware, ensure regular offline backups of critical data, keep all software updated, educate employees on phishing, restrict user access, secure remote desktops with strong authentication, monitor for anomalies, and have a robust incident response plan in place. These proactive measures are crucial for minimizing ransomware risks and protecting your business’s essential operations and data integrity.
To comply with data protection regulations, understand relevant laws, establish strict policies for data collection, storage, and processing, obtain consent from individuals, ensure transparency in data practices, and implement strong security measures. Train staff regularly, conduct audits, and stay updated on regulatory changes to maintain compliance and protect personal data effectively.
A cybersecurity incident response plan should define roles and responsibilities, outline procedures for detecting and assessing incidents, and detail steps for containing, eradicating, and recovering from threats. It should include communication protocols, documentation of actions taken, and a post-incident review process for improvement. Regular training and updates ensure readiness to handle threats, protecting your business and maintaining trust with stakeholders.

